Quantum Cyber GRC
Update solution on July 24, 2024
Quantum computing (QC) has been under development for decades, but according to all informed industry predictions, it will become widely used in just a few years. Its exponentially greater computing power/speed, and a fundamental difference in logic foundation, will offer many transformational opportunities. However, it has long been understood that its greater computational power will also overcome the protection offered by many types of encryption systems currently in use. The encryption systems used to underpin many widely-used communications protocols (securing internet connections, remote access, file transfers, and VPNs) and for encrypting enterprise data and emails, are examples that will need to be replaced.
Furthermore, the future threat to encrypted data is an active risk in the present day, for organisations within industries that need to store data for years (because of compliance requirements, or because it is still valid for business reasons). If data compromised now is still valuable or relevant when QC becomes accessible, bad actors can then decrypt and use the data nefariously. Thus, organisations may incur risk at a future date of ransom situations, and compliance penalties, caused by the protection that is in place right now being inadequate.
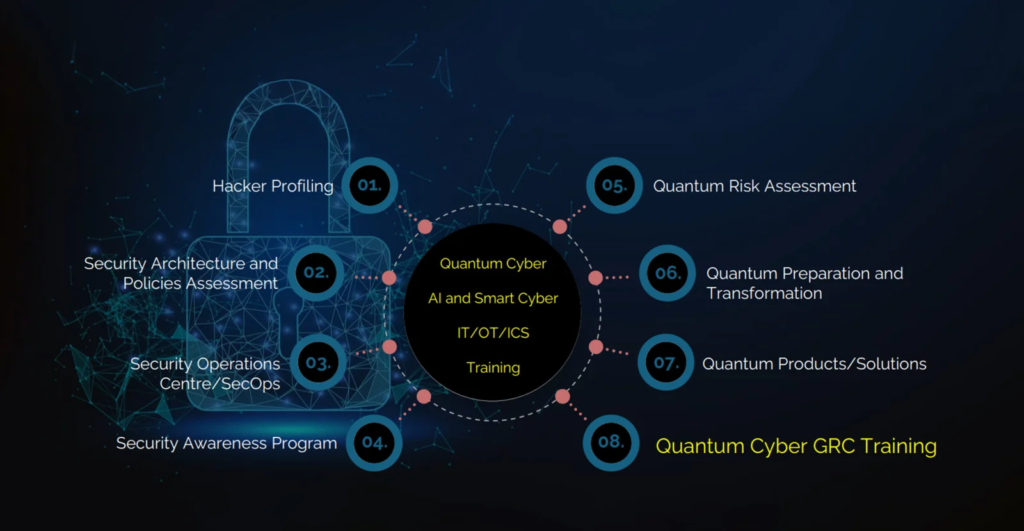
Cystel’s Quantum Cyber GRC services deliver training and tools to enable planning and navigation of the organisation-wide change necessary to counter the threat to current encryption protection from QC.
Four course options are available, for delegates with different responsibilities and perspectives:
- Quantum Cyber GRC Associate, an introduction to management of QC threats from a GRC perspective.
- Quantum Cyber GRC Professional, which focuses more deeply on operational, tactical and strategic best practices.
- Quantum Cyber GRC for Leaders, orienting towards a model that integrates the GRC elements of the technical and organisational change necessary.
- Quantum Cyber Transformation, focusing more closely on putting quantum-ready security in place along with related risk management and policies.
The ‘Leaders’ option can be delivered over 1-2 days, with a broad target audience: C-level executives; heads of cyber/digital/risk/finance/transformation; and cyber/digital technologists.
Customer Quotes
“Quantum computing presents considerable opportunities but also threats. Many industry sectors rely heavily on encryption to protect sensitive information, the exposure of which could cause significant harm to consumers and markets. Addressing this requires a truly collaborative effort to transition to a quantum-secure future.”
Suman Ziaullah, Head of Technology, Resilience and Cyber;
Financial Conduct Authority
Encryption is a key weapon enabling digital delivery of a huge range of processes and services. It underpins foundational characteristics such as communications, identity, data protection, and privacy, without which the ubiquity of digitally-enabled facilities would be limited due to intolerable risk, and lack of market confidence. This widespread use is the reason that replacing methods of encryption is so fundamental and broad an undertaking for organisations – and also why Cystel recommends a GRC-led approach to any organisation tackling the threat of encryption-related risk increasing.
All types of organisation will have to prepare to upgrade, over time, encryption-enabled technologies that underpin their critical business operations and protect their data assets. Planning how an organisation should navigate that (including minimising disruption, risk, and cost) should involve multi-disciplinary collaboration across all parties internally that could be affected. This is the reason that the training provided by Cystel is relevant to very senior organisational roles, as well as more operational and technical roles. Planning will also involve understanding the related plans of all external suppliers, responsible in most organisations for delivery of many business services and their key technology elements. Those suppliers will typically be integrated digitally in ways which will also require the underlying integration technology to be upgraded, and the supporting commercial agreements may also need to be changed.
Whatever the sequence and scale of events during the upgrade of encryption technologies, numerous risks to business operations and continuity will need to be foreseen and managed. Understanding how each risk can affect individual elements of an organisation differently is a key capability of a GRC approach. Another benefit of the approach is to enable monitoring of technology changes impacting organisational compliance negatively, and to ensure that compliance reporting includes any factors relating to the encryption issues. Organisations should be able to analyse and comprehend these risk and compliance factors of the overall encryption upgrade, including how they apply to different areas of the enterprise, and to be able to summarise them accurately for C-level reporting purposes.
The problem of quantum computing compromising current encryption methods is an issue for organisation TODAY, not at some future date. Because the use of encryption is so embedded and fundamental, all organisations are prone to incur risk by failing to conduct detailed analysis and plan how to approach the transition to being secure against quantum-enabled compromise of the current technology.
Cystel has in-depth expertise in this niche security area and has invested in capabilities that can help organisations understand and act in the face of this critical problem. Its choice of a business-led focus on the impact and operations during technology transition is key to organisations avoiding unforeseen and costly outcomes.
Bloor believes that Cystel has scope and depth in its capabilities that put it ahead of larger competitors in helping organisations with this present, and ever more pressing, issue.
Related Company
Connect with Us
Ready to Get Started
Learn how Bloor Research can support your organization’s journey toward a smarter, more secure future."
Connect with us Join Our Community
