K2view Enterprise Data Masking
Update solution on June 4, 2025
What is it?
The K2view Data Product Platform provides a single, foundational platform upon which multiple specialised K2view products are offered, addressing a wide range of enterprise data management challenges. Key products include Test Data Management, Synthetic Data Management, Data Pipelining, Customer 360, and Enterprise Data RAG. In particular, at least for this article, it provides a robust data masking product, K2view Enterprise Data Masking (see Figure 1), offered in support of data security in general and test data management in particular.
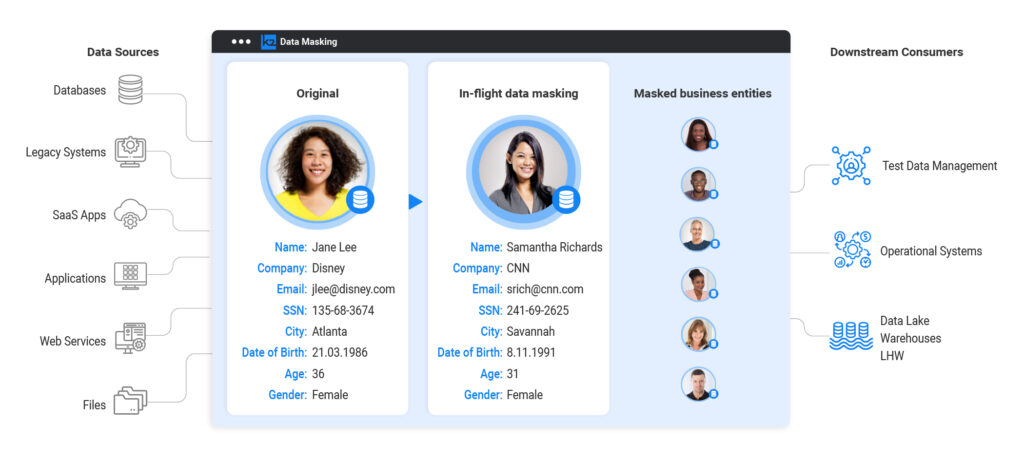
One of the core capabilities of the K2view platform is its ability to organise your data into virtualised Micro-Databases, each one containing all of the information available on a particular business entity (such as a customer). This means that all data related to that entity is unified, and consistently refreshed, within a single (conceptual) location, making it far easier to process and manage that data.
This applies to K2view’s data masking as much as it does to its other data management products. By providing and leveraging 360º views of individual entities, K2view is able to mask your data intelligently, using those entities as vital context to ensure that your masking is effective and comprehensive. It allows you to mask data consistently at the entity level, maintaining relationships present within the entity while anonymising the information involved. For example, if you are masking a customer entity with age and date of birth fields, changing one will create a corresponding change in the other. This applies even if the fields in question originate in different physical systems, because they have already been centralised into one Micro-Database. Moreover, since K2view masks each entity individually, there is relatively little risk of creating unintended patterns in the data that can contribute to reidentification.
Business entities also help with discoverability, by providing you with identifying information that you can use to search for additional, relevant data. For instance, if an entity contains an ID number, you can search for that number across your data sources (which could include structured, unstructured, and/or semi-structured data), and any results will likely correspond to the original entity. They can then be masked appropriately. Business entities also facilitate in-flight data masking, without having to persist the original, unmasked data in an interim, staging database. This eliminates the risk of maintaining unmasked data in lower environments, even temporarily.
What does it do?
Data processes in the K2view platform, such as those required for data masking, generally consist of automated flows (Broadway flows, in K2view nomenclature) made up of a series of steps (Stages) populated with actions (Actors). Broadway flows are designed visually, and after execution you can view data flowing through them in real time. They can be created manually, by using drag and drop, or automatically, by communicating in natural language with an AI chatbot.
In a data masking context, the Actors would be masking functions, applied to various fields imported into the Broadway flow. Over a hundred prebuilt masking and other anonymisation functions are provided for this purpose, and if that is not enough you can build your own, custom functions. You can also supply these functions with access to business entity data beyond the data to be masked, providing additional context that allows for more thorough identification, and semantic masking, of sensitive data. For instance, a customer entity might contain a customer status field (such as “Bronze”, “Silver”, or “Platinum”), which is dependent on the customer’s account balance. Masking the customer status would require the account balance to be adjusted accordingly so that the resulting data is valid.
Data masking using K2view is both format-preserving and consistent over different systems and formats. This includes document formatting and similar. In addition, masking is consistent for the same entity over multiple runs. The masking process can leverage API integration for a variety of purposes: for instance, it can be used to gather valid (or, if required, invalid) address data that is consistent with any other geospatial data in the masked entity. You can also move your data (from a production to a test environment, for example) as part of the masking process. While the company primarily offers static masking, dynamic masking is available too, which will anonymise your data in real time based on the roles and/or attributes of the user attempting to access it.
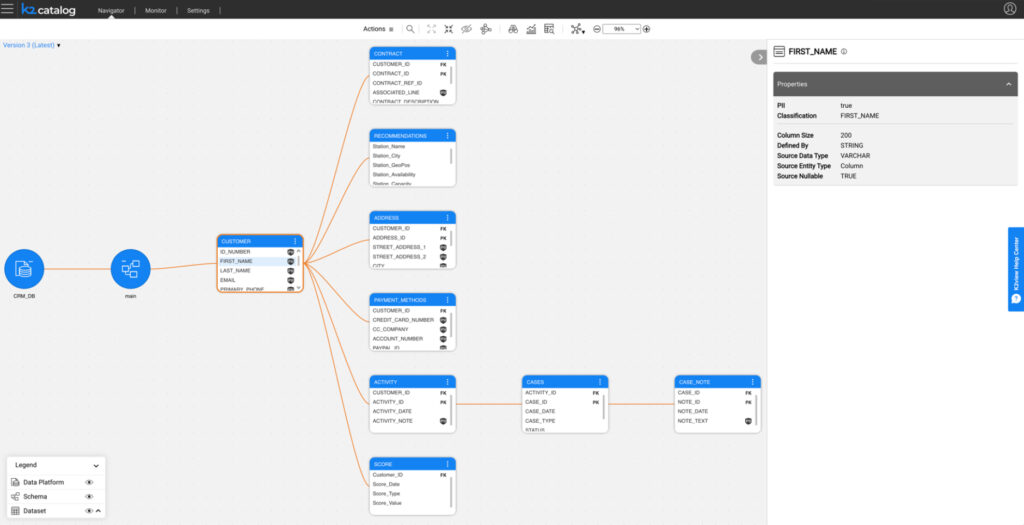
K2view Enterprise Data Masking provides a data catalogue (shown in Figure 2) that is designed primarily to facilitate sensitive and PII data discovery and classification, while integrating with more fully-fledged data catalogues if and when they are present. This catalogue provides functionality for identifying and classifying your data (notably including sensitive data) by examining the data itself, its associated metadata, and its interactions with your data sources. Sensitive data discovery is performed using predefined regular expressions and supported LLMs (typically deployed on premises due to security considerations). Data masking Broadway flows can be assigned to each data classification, which then act as a default masking algorithm for that type of data. You can also configure each algorithm to determine whether it masks uniquely, consistently, or neither; whether it is provided with business entities for additional context; what kind of environment it is designed for; and so on. Moreover, this configuration – and indeed, the catalogue as a whole – is easy to manage, even for nontechnical users, allowing them to drive the masking process if they so choose. Similarly, there is a self-service interface for actioning your masking processes (either on an entire database or a subset). Alternately, you can run them on a schedule.
Why should you care?
As with much of the functionality that K2view offers, business entities play a key role in its data masking success. By leveraging these unified, virtualised Micro-Databases as part of its data masking processes, it is able to both find and mask sensitive significantly more effectively, with significant additional context to inform its automated processes. This context enables more complete sensitive data discovery and more consistent and universal data masking, while also enabling you to uniquely mask each entity if you so choose. Business entities also serve to centralise relevant data from any number of different systems, allowing you to mask consistently and holistically across your organisation. We have already discussed the hows and whys of masking using business entities previously in this paper, so we will not further belabour the point here, but suffice it to say that the use of business entities is a very substantial differentiator for K2view’s data masking offering.
Past that, the K2view’s data masking product offers highly adaptable data masking that is resilient in the face of changes to the masking methodology employed and the underlying data that is being masked. Indeed, this dovetails with its self-service, user-friendly, and highly visual data catalogue interface, making it possible for your data masking processes to be driven primarily by your business users (such as your data security team) while leaving the implementation details to your technical users. This should be very much appreciated, as data masking is fundamentally a compliance, and therefore business, concern.
The bottom line
K2view’s data masking product is very substantial. As always, its use of business entities is a significant differentiator, but even apart from that we are impressed by the overall quality, completeness, and usability of its offering.
Related Company
Connect with Us
Ready to Get Started
Learn how Bloor Research can support your organization’s journey toward a smarter, more secure future."
Connect with us Join Our Community
